Cyber Threats Are Evolving—Is Your Defense Strategy Keeping Up?
In today’s ever-evolving digital landscape, traditional cybersecurity strategies are no longer enough to combat the rising tide of sophisticated cyber threats. The reactive approach of Vulnerability Management (VM) and Attack Surface Management (ASM) leaves gaps in security postures that cybercriminals exploit. This is where Continuous Threat Exposure Management (CTEM) comes into play—a proactive and dynamic approach designed to stay ahead of emerging threats.
As a leading Virtual CISO (vCISO) for over 50 organizations, I, Deepak Kumar Nath, have seen firsthand how businesses struggle with outdated security frameworks. My expertise in securing enterprises across various industries, from finance to healthcare, has shown that CTEM is the future of cybersecurity.
In this guide, we’ll explore why CTEM is essential, how it differs from traditional frameworks, and how businesses should adopt it to strengthen their cybersecurity defenses.
What is Continuous Threat Exposure Management (CTEM)?
Introduced by Gartner in 2022, Continuous Threat Exposure Management (CTEM) is a strategic approach that provides organizations with a continuous, real-world understanding of their cyber risks. It goes beyond patching vulnerabilities and provides real-time insights into how attackers could exploit an organization’s security gaps.
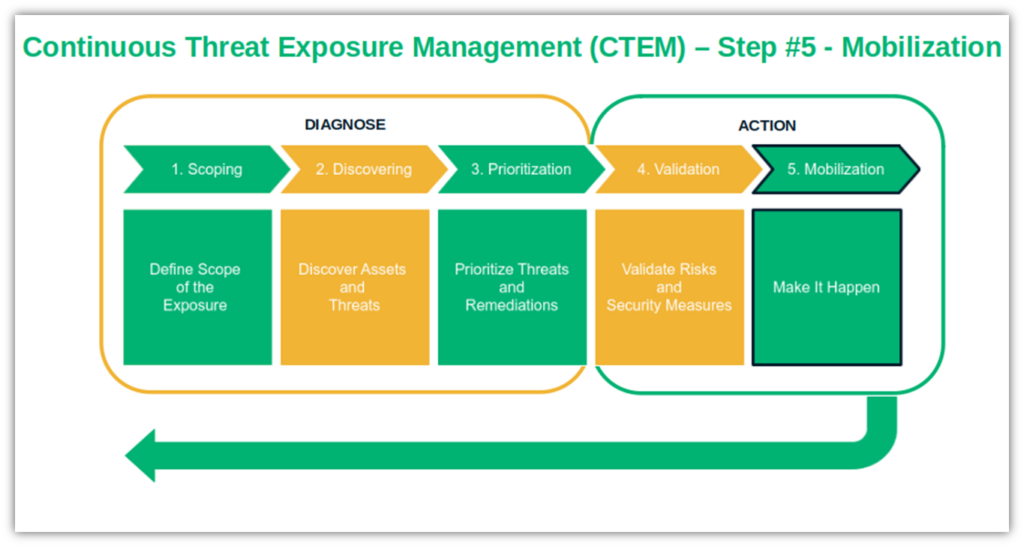
The Five Phases of CTEM
CTEM follows a structured five-phase model:
- Scoping – Identifying all potential cyber threats based on business risk priorities.
- Discovery – Mapping all assets, including external and internal attack surfaces.
- Prioritization – Analyzing threats based on their potential business impact.
- Validation – Running simulated attacks, penetration tests, and threat emulation.
- Mobilization – Strengthening defenses by continuously optimizing security measures.
Unlike traditional models, CTEM does not operate in silos. It combines the best aspects of Vulnerability Management (VM) and Attack Surface Management (ASM) while introducing continuous threat validation, attack simulation, and real-time monitoring.
Why Traditional Security Frameworks Are Not Enough
While VM and ASM have their advantages, they fall short in key areas:
1. Vulnerability Management (VM) Limitations:
- Focuses only on known vulnerabilities within internal infrastructures.
- Reactive in nature—patching vulnerabilities only after discovery.
- Limited scope in detecting sophisticated threats.
2. Attack Surface Management (ASM) Limitations:
- Provides visibility into external-facing assets but lacks continuous validation.
- Does not actively test security controls against real-world attack scenarios.
- Cannot simulate threats or assess impact on business operations.
CTEM combines the strengths of VM and ASM while addressing their limitations. It enables businesses to proactively assess, detect, and neutralize threats before they escalate into full-blown cyber incidents.
Why CISOs and Organizations Must Adopt CTEM
For today’s Chief Information Security Officers (CISOs), ensuring that security efforts align with business goals is crucial. Unlike traditional security measures, which often slow down business operations, CTEM strikes a balance between security and business efficiency.
Key Benefits of CTEM Adoption:
✅ Continuous Risk Assessment – Ensures security is always aligned with real-time business needs.
✅ Real-Time Threat Simulation – Uses red teaming, penetration testing, and attack simulations to validate security controls.
✅ Better Incident Response – Enhances SOC capabilities by providing real-time threat intelligence and automation.
✅ Business-Centric Security Approach – Helps CISOs prioritize threats based on their actual business impact.
✅ Cost-Effective Security – Reduces financial losses from cyber incidents by proactively mitigating risks.
How Companies Should Implement CTEM
Adopting Continuous Threat Exposure Management (CTEM) requires a structured, strategic approach. Here’s how businesses should integrate CTEM into their cybersecurity framework:
1. Start with a Cybersecurity Gap Assessment
Before implementing CTEM, companies must conduct a comprehensive security assessment to identify existing vulnerabilities and gaps.
2. Integrate with Existing Security Tools
CTEM doesn’t replace VM or ASM—it enhances them. Companies should integrate CTEM solutions with existing security tools like SIEM, EDR, and SOC platforms.
3. Implement Continuous Threat Simulations
Businesses should regularly simulate cyberattacks (red teaming, breach-and-attack simulations) to test the effectiveness of their security defenses.
4. Automate Threat Prioritization and Response
Using AI-driven threat intelligence, companies should automate risk prioritization to focus on high-impact vulnerabilities first.
5. Train Security Teams for CTEM Implementation
Investing in cybersecurity training for in-house teams ensures that organizations stay ahead of evolving threats. As a leading vCISO, I personally recommend hands-on cybersecurity training to strengthen internal security teams.
CTEM: The Future of Cybersecurity
As cyber threats become more advanced, businesses must adopt a continuous, proactive security approach like CTEM to stay ahead. By integrating CTEM with existing security frameworks, organizations can ensure better threat detection, faster incident response, and a business-aligned security strategy.
With my extensive experience as a vCISO for 50+ organizations, I have helped enterprises across industries enhance their security posture using CTEM principles. If you want to safeguard your organization against evolving cyber threats, now is the time to implement a proactive cybersecurity strategy.
Need Expert Guidance? Let’s Secure Your Business Today!
If you’re ready to integrate CTEM into your cybersecurity framework, my team and I can help you assess, implement, and optimize your security posture.
📩 Contact Deepak Kumar Nath for expert cybersecurity solutions today!





