Insights by Deepak Kumar Nath
In yet another alarming discovery, security researchers have uncovered vulnerabilities in Xerox VersaLink C7025 Multifunction Printers (MFPs) that could allow attackers to capture Windows Active Directory credentials. This flaw, if exploited, could lead to serious security breaches, allowing cybercriminals to move laterally within an organization's infrastructure and compromise critical systems.

Understanding the Threat
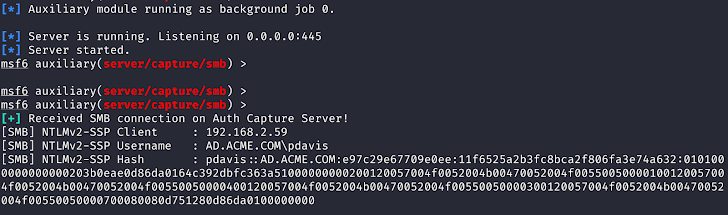
The security vulnerabilities were disclosed by Rapid7 researcher Deral Heiland, who identified that attackers could exploit pass-back style attacks through Lightweight Directory Access Protocol (LDAP) and SMB/FTP services. These attacks manipulate the printer's configuration to send authentication credentials back to a rogue actor.
“If a malicious actor can successfully leverage these issues, it would allow them to capture credentials for Windows Active Directory. This means they could then move laterally within an organization's environment and compromise other critical Windows servers and file systems,” Heiland explained.
Identified Vulnerabilities
The following security vulnerabilities have been discovered in Xerox VersaLink printers, particularly affecting firmware versions 57.69.91 and earlier:
- CVE-2024-12510 (CVSS Score: 6.7) – Pass-back attack via LDAP
- CVE-2024-12511 (CVSS Score: 7.6) – Pass-back attack via the user’s address book
How the Attacks Work
- CVE-2024-12510: A rogue server could intercept authentication data if an attacker modifies the LDAP configuration on the printer. This flaw requires prior access to the LDAP settings page and that LDAP is used for authentication.
- CVE-2024-12511: Attackers could manipulate the user address book configuration to modify the SMB or FTP server’s IP address. By redirecting authentication requests to a malicious server, they can harvest credentials used during file scan operations.
For these attacks to be successful, the attacker must gain access to the printer’s physical console or remotely control it via the web interface. If user-level remote control access is enabled, an attacker may not even require admin privileges.
Security Patches & Mitigation Strategies
Xerox has acknowledged these vulnerabilities and has released Service Pack 57.75.53 to address the issue for VersaLink C7020, 7025, and 7030 series printers. Organizations are strongly advised to update their printer firmware immediately to prevent exploitation.
However, if immediate patching is not feasible, users should implement the following security measures:
- Set a strong and complex password for the admin account.
- Avoid using Windows authentication accounts with elevated privileges on the printer.
- Disable remote control console access for unauthenticated users.
The Bigger Picture: Cyber Threats Are Rising
This discovery follows another recent revelation of an unauthenticated SQL injection vulnerability in widely deployed healthcare software HealthStream MSOW (CVE-2024-56735). This flaw could allow attackers to compromise the database of 23 healthcare organizations, exposing sensitive patient data to malicious actors.
Cyber threats like these underscore the importance of continuous monitoring, proactive vulnerability management, and rapid patching. At Threatsys, we specialize in penetration testing, vulnerability assessments, and cybersecurity compliance to help businesses and government entities stay protected.
Final Thoughts
As organizations become more reliant on connected devices and cloud services, cybersecurity risks continue to evolve. The Xerox printer vulnerabilities highlight how even peripheral IT assets can become entry points for cyberattacks. Staying ahead of these threats requires constant vigilance, proactive defense mechanisms, and expert guidance.
For tailored cybersecurity solutions, risk assessments, and compliance support, get in touch with Deepak Kumar Nath and our team at Threatsys. Secure your organization before hackers strike!